Introduction to Opera Browser
Opera debuted in 1994 and quickly gained popularity for its innovative features, including tabbed browsing, a built-in email client, and a focus on customization. It was known for its clean interface and fast performance, even on slower computers. However, in recent years, Opera's market share has declined as competition from Chrome, Firefox, and Safari has intensified. This has led to some significant changes in the company's direction.
Understanding the My-Flow Feature
My-Flow was a convenient feature designed to streamline the user experience across devices. It aimed to bridge the gap between your smartphone and your desktop computer, allowing you to seamlessly share messages and files. This functionality was achieved through a built-in extension that integrated with the Opera mobile app. Unfortunately, this seemingly harmless feature harbored a critical security flaw that threatened users' safety.
The Zero-Day Vulnerability: (MyFlawCross Platform 0-Day RCE Vulnerability)
A zero-day vulnerability is a critical security flaw in software that the software vendor is unaware of. This means there's no patch or update available to fix the problem, leaving users vulnerable until a fix is developed and deployed. In the case of Opera's MyFlow feature, the vulnerability allowed attackers to bypass a crucial security measure known as a sandbox.
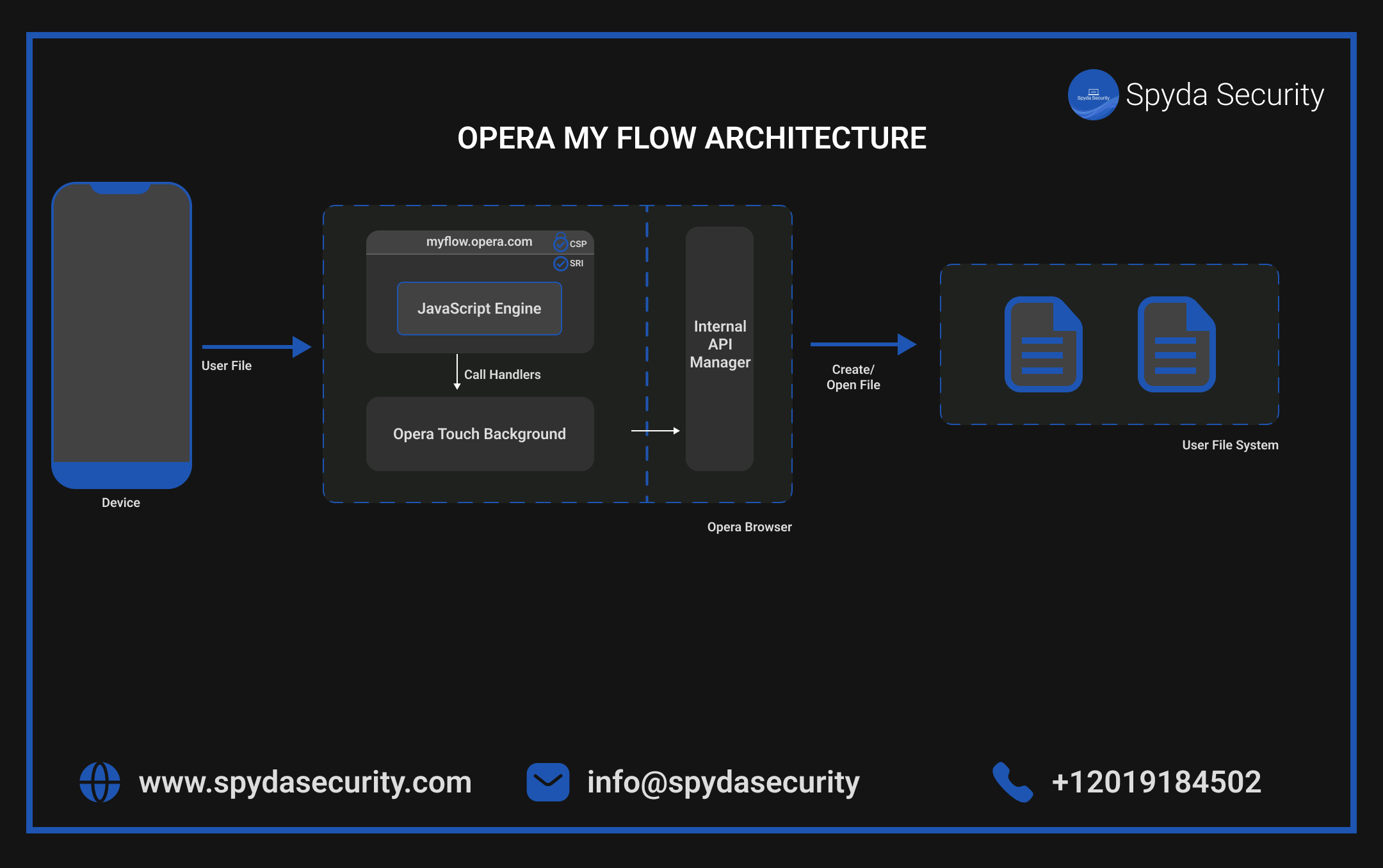
What is a Sandbox?
A sandbox is a virtual environment that isolates a program from the rest of the computer system. This isolation helps prevent malicious code from accessing and damaging the user's files, applications, and operating system. Web browsers typically use sandboxes to restrict the programs running within web pages from interacting with the user's device.
Bypassing the Sandbox with MyFlaw
The MyFlaw vulnerability allowed attackers to craft malicious code that could exploit a weakness in the MyFlow extension. This malicious code could then trick the browser into running it outside of the sandbox, granting it unauthorized access to the user's system.
Remote Code Execution (RCE) Attacks
With this unauthorized access, attackers could launch a Remote Code Execution (RCE) attack. An RCE attack allows attackers to remotely execute (or run) arbitrary code on the victim's machine. In simpler terms, this means the attacker could take complete control of the affected device, potentially allowing them to:
- Steal sensitive data like login credentials, financial information, or personal documents.
- Install additional malware or spyware.
- Disrupt or disable critical system functions.
- Use the compromised device to launch attacks on other computers.
Exploitation Techniques
Attackers could leverage this flaw to create and activate malicious files directly on the user's operating system. The automatic encryption feature of the My-Flow extension, designed to secure file transfers, could inadvertently conceal these harmful payloads. This creates an opportunity for social engineering attacks, where users are tricked into downloading and executing malicious files.
Potential Risks and Vulnerabilities
- Remote Code Execution (RCE): Attackers could gain complete control of the victim's machine.
- File System Access: Attackers could steal or destroy data by accessing and modifying files.
- Sandbox Escape: Bypassing the browser's security sandbox grants attackers higher privileges, potentially compromising the entire system.
- Social Engineering: The My-Flow vulnerability could be used to distribute malware through social engineering tactics.
- Encrypted Payload Concealment: Automatic encryption makes it harder to detect malicious files sent via My-Flow.
Beyond Security: Trend Chasing and User Monetization
While the security flaw has been addressed, concerns linger regarding Opera's business practices. Here's what the report by Hindenburg Research alleges:
Trend Chasing and User Monetization
- Shifting Focus: Opera is accused of prioritizing more profitable ventures over maintaining and growing its browser user base.
- Aggressive Monetization: The company allegedly seeks to maximize revenue from its remaining users.
Shift to Predatory Loan Apps
- Market Shift: Facing competition, Opera reportedly shifted focus to mobile apps, specifically financial services.
- Predatory Lending: The company is accused of developing and marketing loan apps with exorbitant interest rates and short repayment terms, targeting vulnerable populations.
- Deceptive Practices: The report alleges misrepresentation of loan terms to comply with app store regulations.
Targeted Demographics
Vulnerable Populations: The loan apps reportedly targeted people in Kenya, India, and Nigeria, raising ethical concerns.
While Opera has addressed the security vulnerability, the report on its business practices raises ethical concerns. Users seeking a secure and trustworthy browser may want to consider alternatives until Opera regains user trust.